Resources
Implementing new cybersecurity processes and technologies requires research and due diligence. Our team has delivered cybersecurity services in some of the most demanding environment for over a decade. The resources on this page will help you better understand how utilizing various cyber security tools and strategies will benefit your security operations team.
Articles | Case Studies | Datasheets | Videos
Articles
Accelerating Security Breach Remediation with AI-Powered Incident Response
In this article, we explore how incorporating AI/ML capabilities can revolutionize a cybersecurity team’s incident response processes.
Automating Incident Response: A Use Case for Streamlined Remediation of Phishing Attacks
In this article, we explore a use case that highlights how organizations can use SOAR to automate incident response to improve the remediation of phishing attacks.
Building Resilient Data Protection: The Benefits of Automated DLP
In this article, we discuss the need for data loss prevention (DLP) measures and how pairing a DLP solution with security orchestration, automation and response (SOAR) platform can exponentially enhance your incident response capabilities.
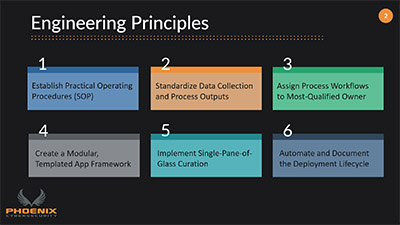
Six Essential Engineering Principles for Developing Advanced Security Automations
In this article, we discuss six steps that should be followed when using a security automation, orchestration and response (SOAR) platform to implement security automation workflows.
Struggling Under the Barrage of SIEM Alerts? Automate to Mitigate Using SOAR
In this article, we discuss how SIEM solutions can produce an overwhelming number of alerts and how leveraging automated responses to threats using a SOAR platform can help to alleviate this issue.
The Evolution of Threat Intelligence: Empowering Organizations with SOAR
In this article, we dive into the dynamic landscape of threat intelligence and explore how the adoption of security orchestration, automation and response enhances threat intel operations and enables organizations to proactively respond to potential security threats.
The Power of Automated Threat Hunting
In this article, we discuss how the use of security automation has become pivotal in expediting threat hunting to streamline processes, analyze data at scale, and respond rapidly to potential threats.
Case Studies
Phoenix Cyber delivers groundbreaking privacy compliance application for Federal Government client
This case study details how Phoenix Cyber delivered a groundbreaking privacy compliance application for a Federal Government client that increased efficiency over 250% by automating privacy law and regulation compliance around personally identifiable information.
Phoenix Cyber delivers cybersecurity project management and security engineering expertise to Southwestern U.S.-based Integrated Health System
This case study describes how Phoenix Cyber provided cybersecurity project management and security engineering expertise to a Southwestern United States Integrated Health System throughout an ongoing 10-year relationship.
Datasheets
Federal Capabilities Statement
The Federal Capabilities Statement describes our expertise, capabilities, services, federal contract vehicles and past performance delivering cybersecurity services and solutions to U.S. Federal Government clients.
Enterprise Capabilities Statement
The Enterprise Capabilities Statement describes our expertise, capabilities, services, and industry certifications for delivering cybersecurity services and solutions to enterprise clients within the United States.
Videos
Next-Level Data Loss Prevention with Low-Code Security Automation
Watch this on-demand webinar replay to see how low-code security automation can help you streamline your DLP processes and reduce the risk of data loss.
Security Operations Center (SOC) Automation: Real World ROI
This 9-minute presentation shows how Security Orchestration, Automation and Response (SOAR) can reduce the time SOC analysts spend processing tickets—decreasing the organization’s Tier-1 workload by 75%.
Security Orchestration, Automation and Response (SOAR) Engineering Principles
This 5-minute video will introduce you to the six security engineering principles that we follow when implementing Security Orchestration, Automation and Response (SOAR) solutions.